Tisalabs Knowledge Base
Executive impersonation attacks are considered a significant threat, as trust and authority are exploited by cybercriminals. In this tutorial, guidance will be provided on executing an executive impersonation phishing campaign, simulating an email from the CEO requesting sensitive information. By following these steps, organizations can assess their vulnerability to such attacks and strengthen their cybersecurity measures.
To initiate the campaign, a sender profile resembling the CEO's email address must be established, along with a convincing email template.
Step 1: Sender Profile Creation A sender profile will be configured using the CEO's email address to enhance the authenticity of the phishing email.
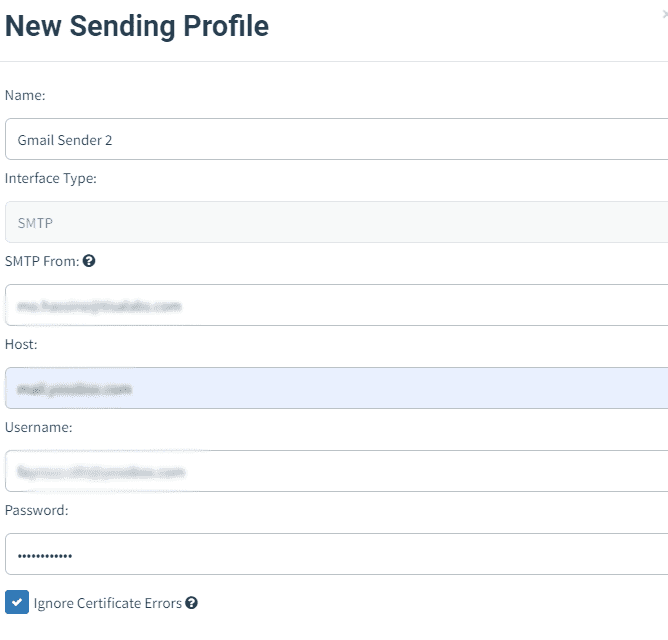
Step 2: Email Template Crafting An email template will be designed requesting sensitive information from employees, mimicking the urgency and tone of communication typical of executive requests.
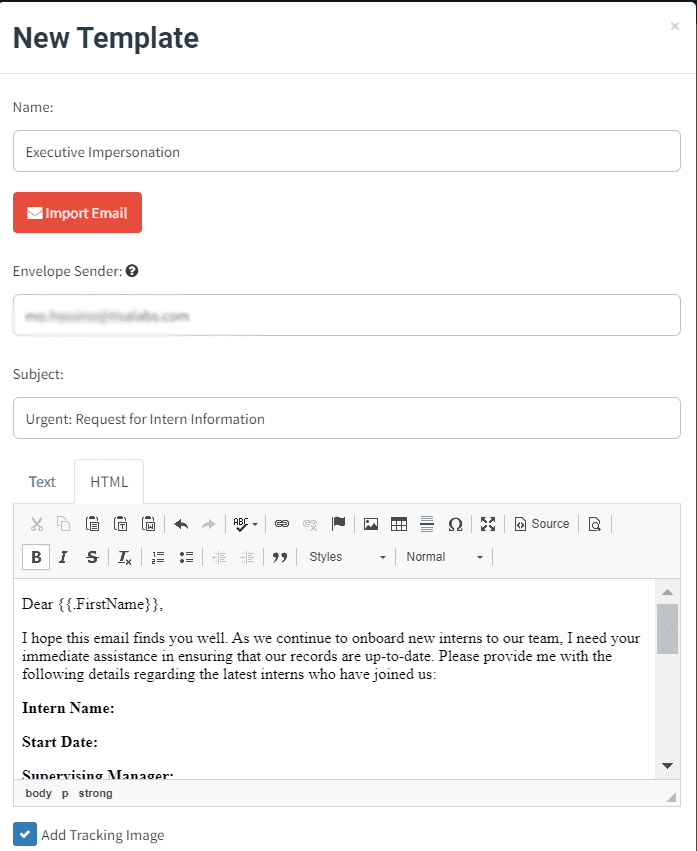
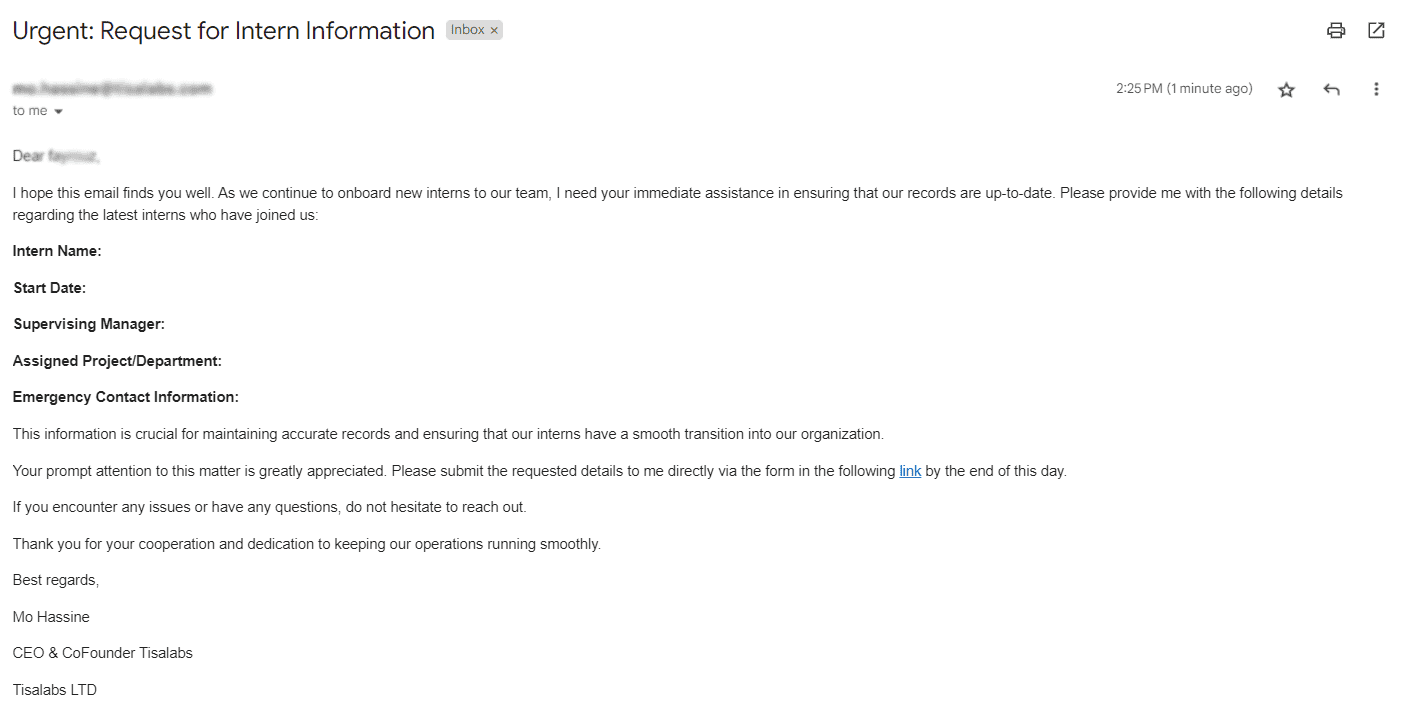
This is the email template that we did get:
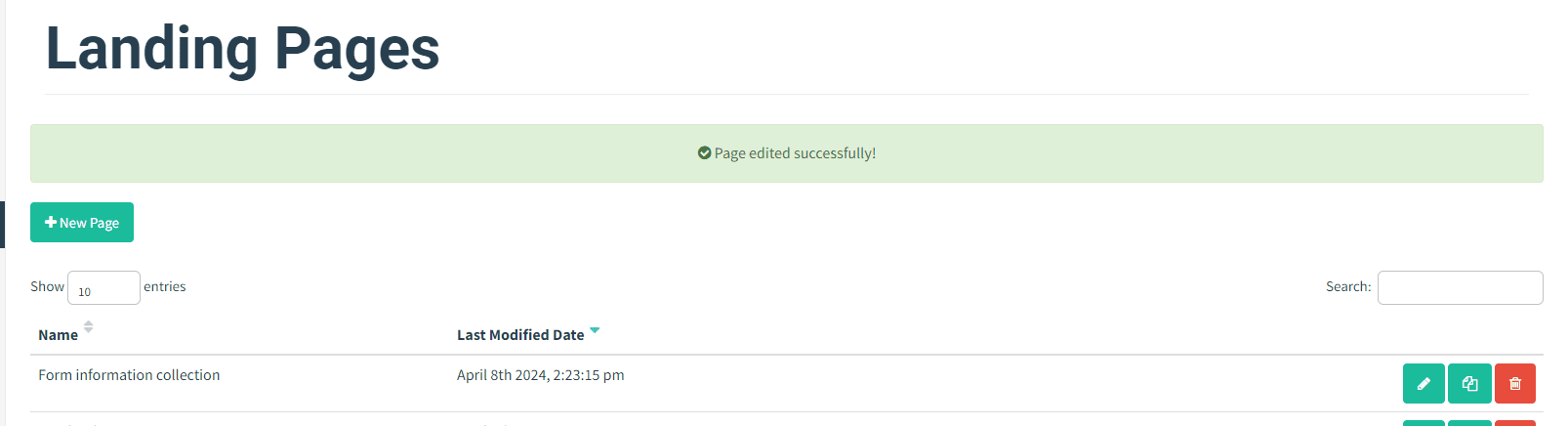
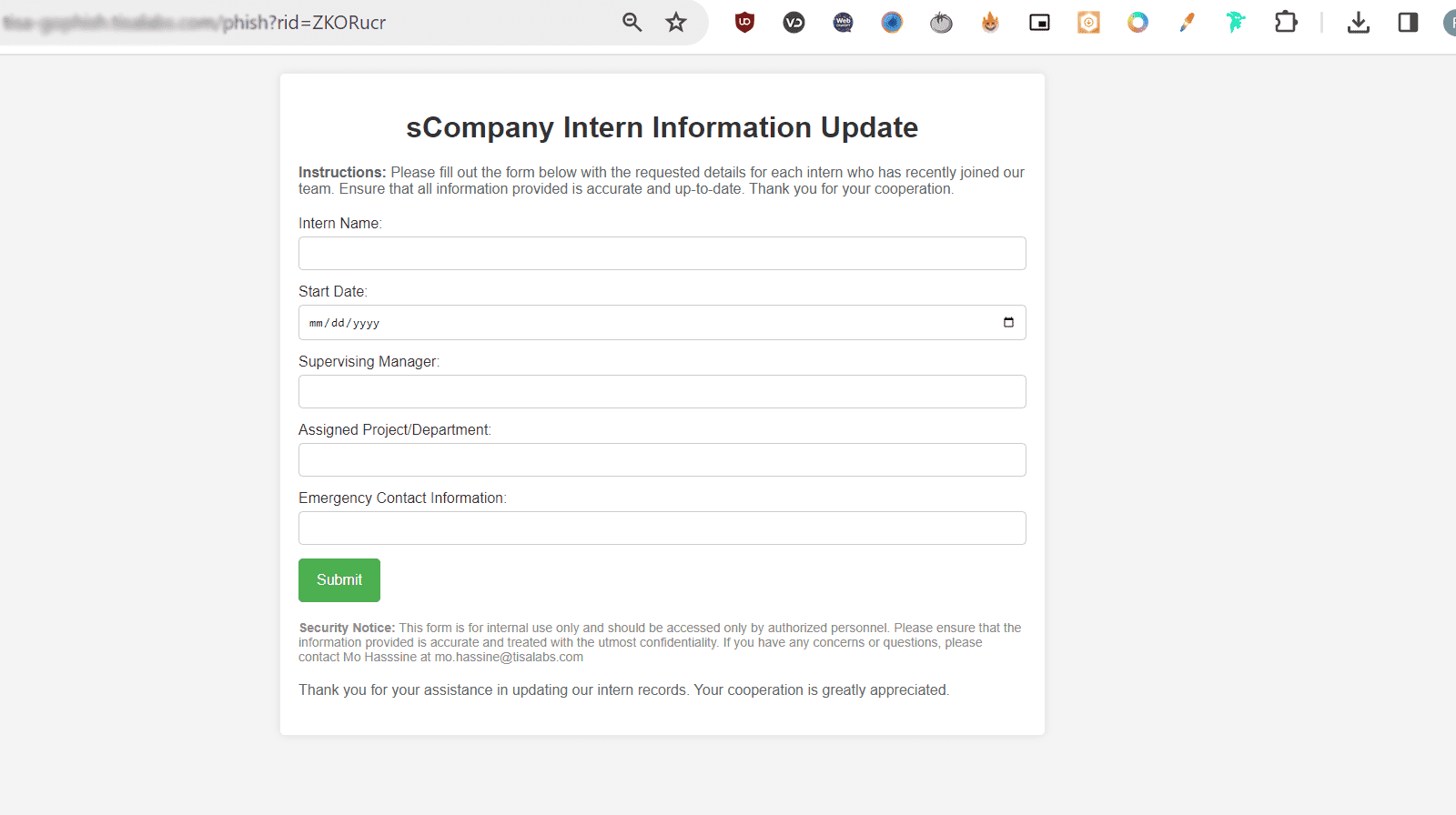
A landing page will be created to capture sensitive information requested in the email.
Step 1: Landing Page Development A basic landing page will be designed displaying a form for employees to submit the requested information.
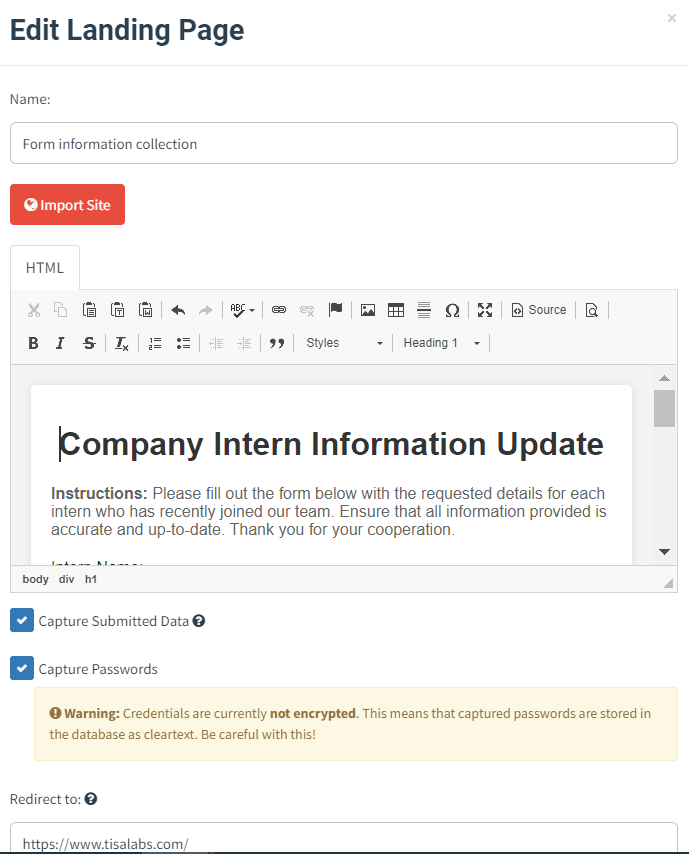
Step 2: Form Submission Process Upon form submission, users will be redirected to a legitimate-looking webpage to avoid suspicion.
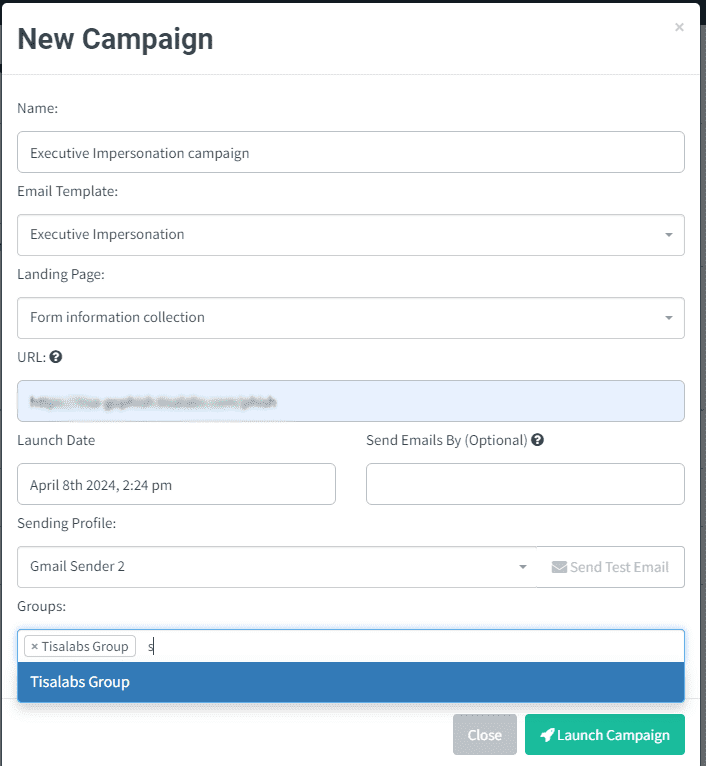
With all components in place, the phishing campaign can be launched.
Step 1: Campaign Launch The campaign will be initiated, and the phishing email will be sent out to targeted employees.
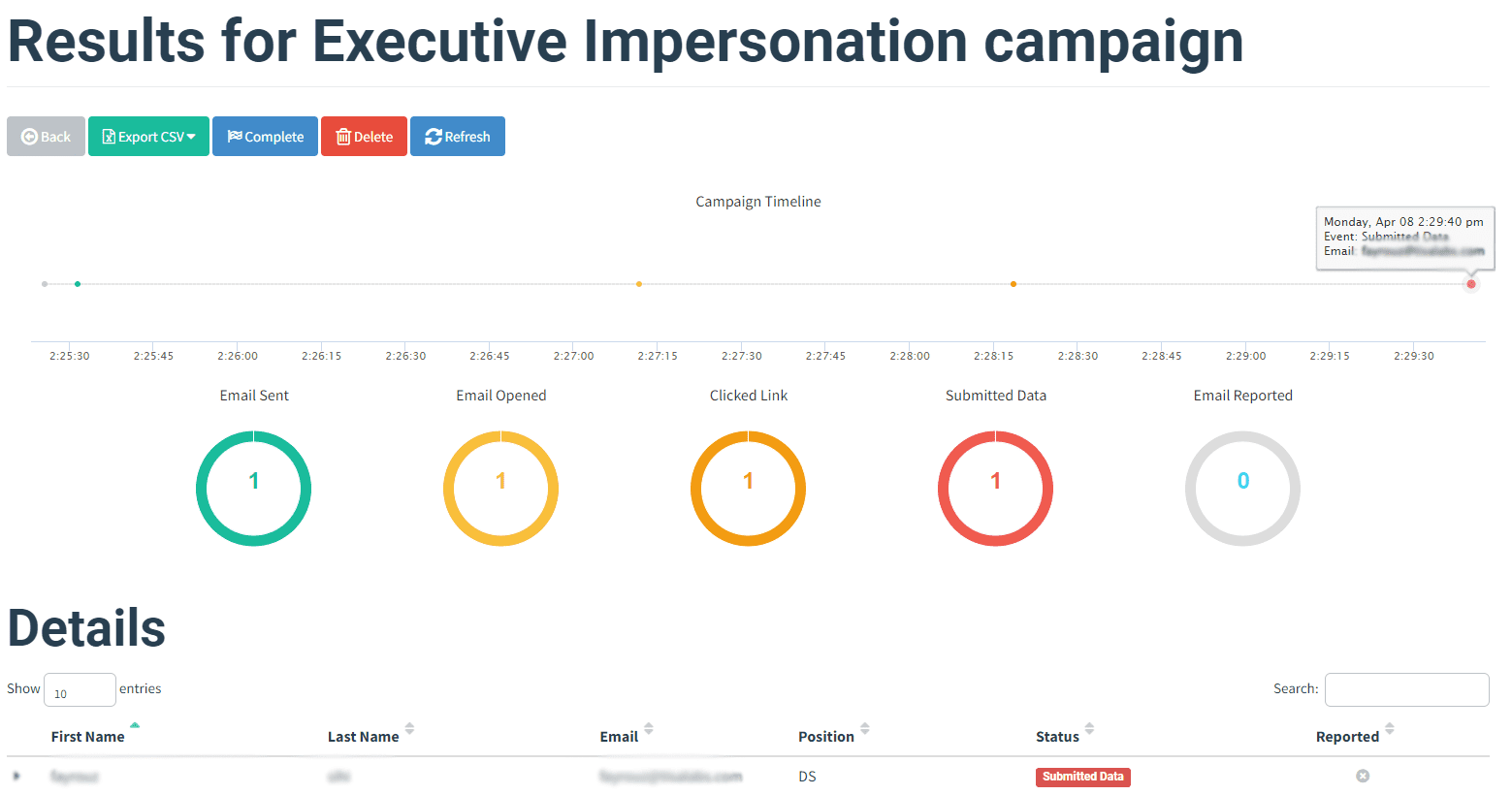
Step 2: Campaign Progress Monitoring The campaign's progress will be monitored from the dashboard, tracking email open rates and user interactions.
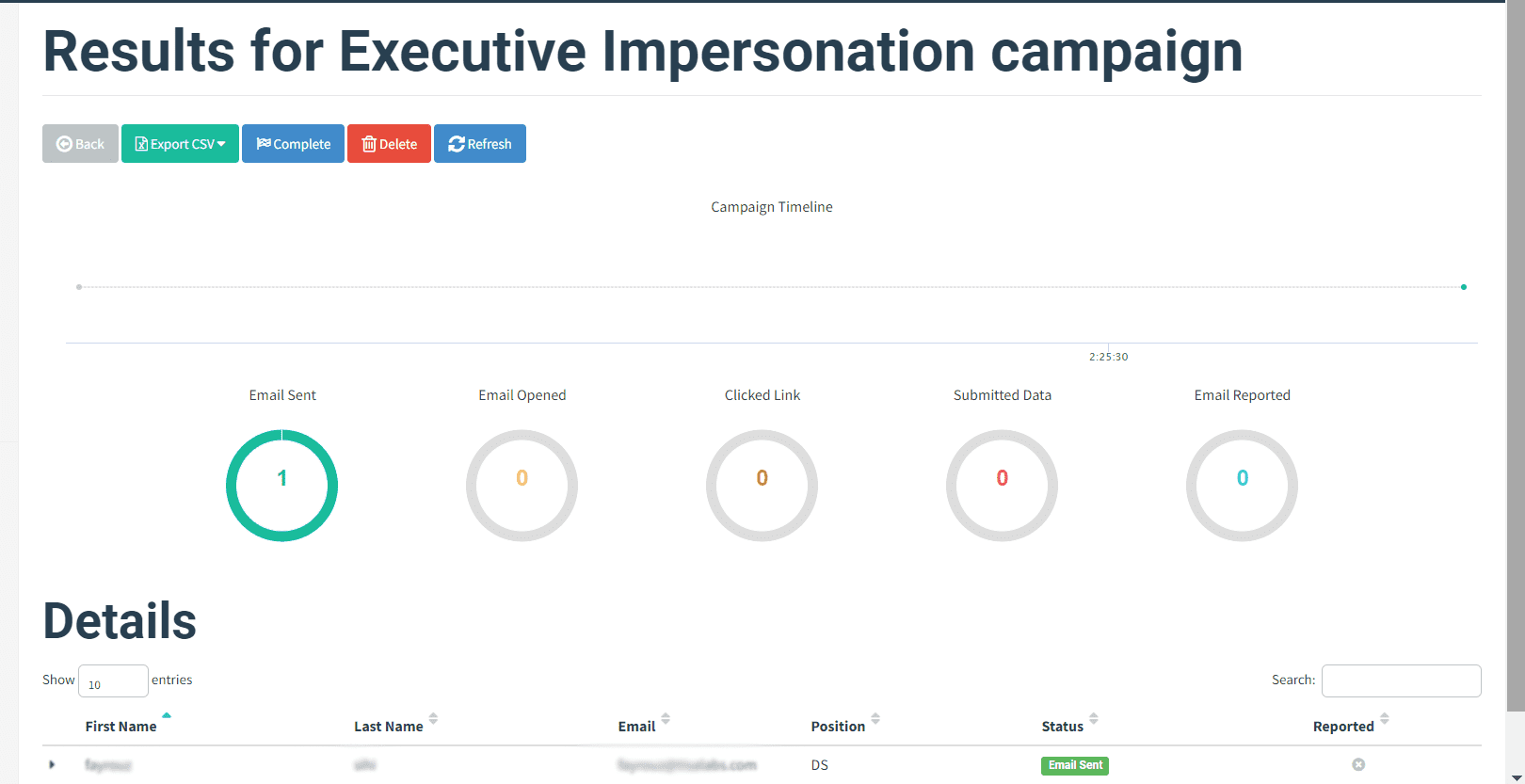
The outcomes of the phishing campaign will be evaluated to assess its effectiveness.
Step 1: Email and Landing Page Inspection The appearance of the phishing email in recipients' inboxes will be inspected, and the authenticity of the landing page will be reviewed.
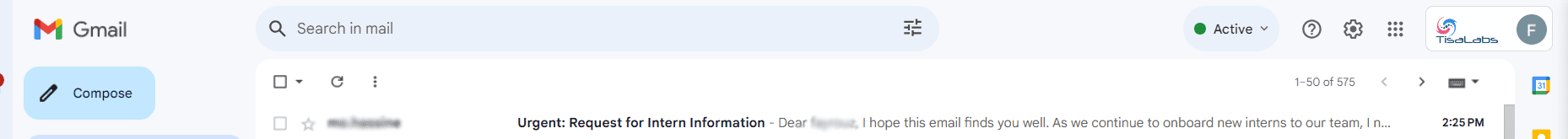
and this is the content of the email when the target user opens it:
Step 2: User Interaction Analysis User interactions, including form submissions, will be analyzed to gauge the success of the campaign.
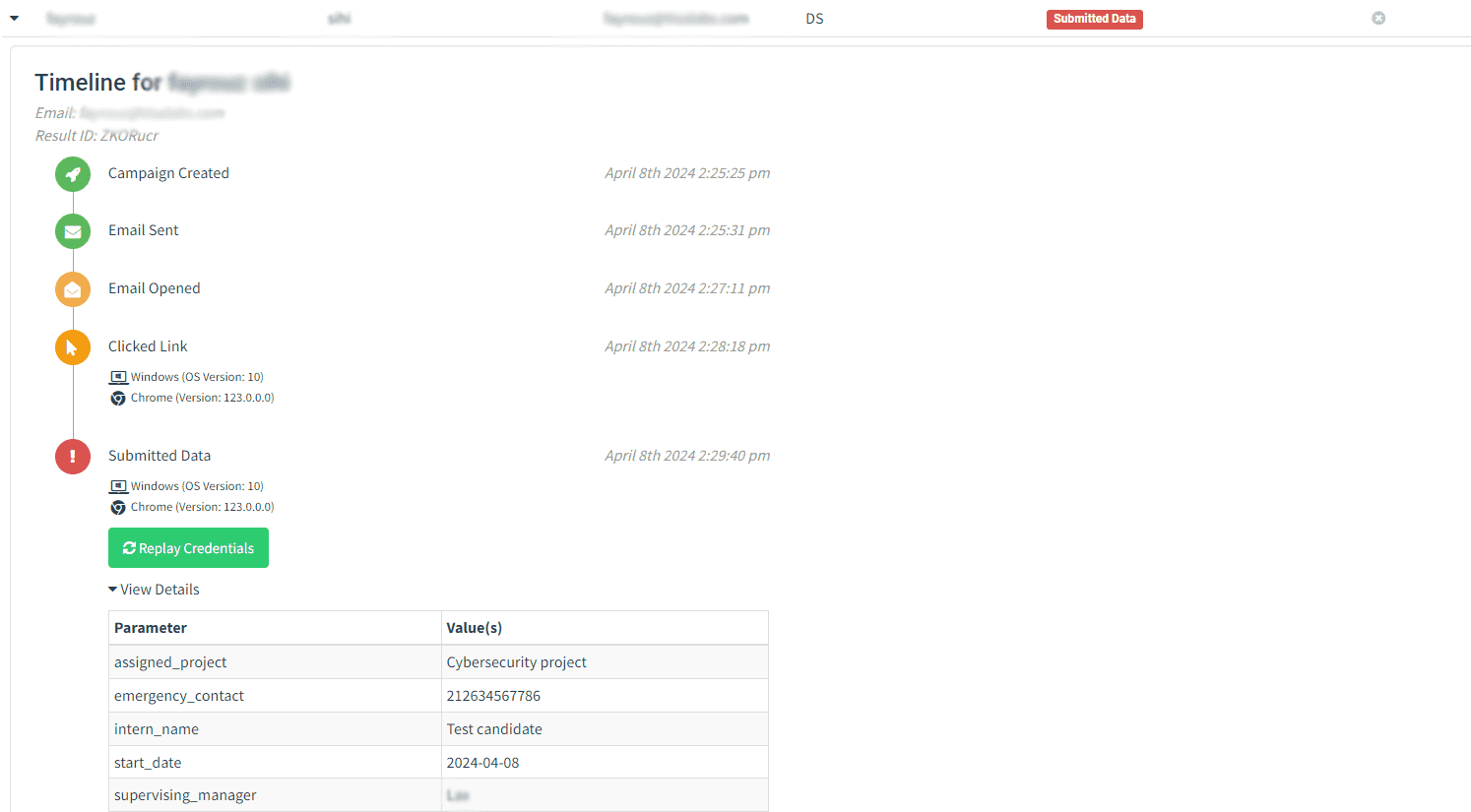
Step 3: Data Collection and Analysis The data collected from user submissions will be examined to understand the extent of information compromised.
and following are the details of the data that we did capture using the form:
Conducting an executive impersonation phishing campaign provides valuable insights into organizational vulnerabilities. By following this tutorial, organizations can better understand the risks posed by such attacks and implement necessary security measures to mitigate them.
If you still can't find an answer to what you're looking for, or you have a specific question, open a new ticket and we'd be happy to help!
Contact Us