Tisalabs Knowledge Base
In this tutorial, we'll explore how to execute a phishing campaign with malicious attachments to test user susceptibility to opening such files. We'll guide you through the process of creating convincing emails with attached files and setting up a landing page to encourage user interaction.
Begin by composing a phishing email containing a malicious attachment. This attachment could simulate malware or ransomware to assess user responses.
Step 1: Create Email Content
Craft a persuasive email enticing users to open the attachment, such as an invoice or urgent document.
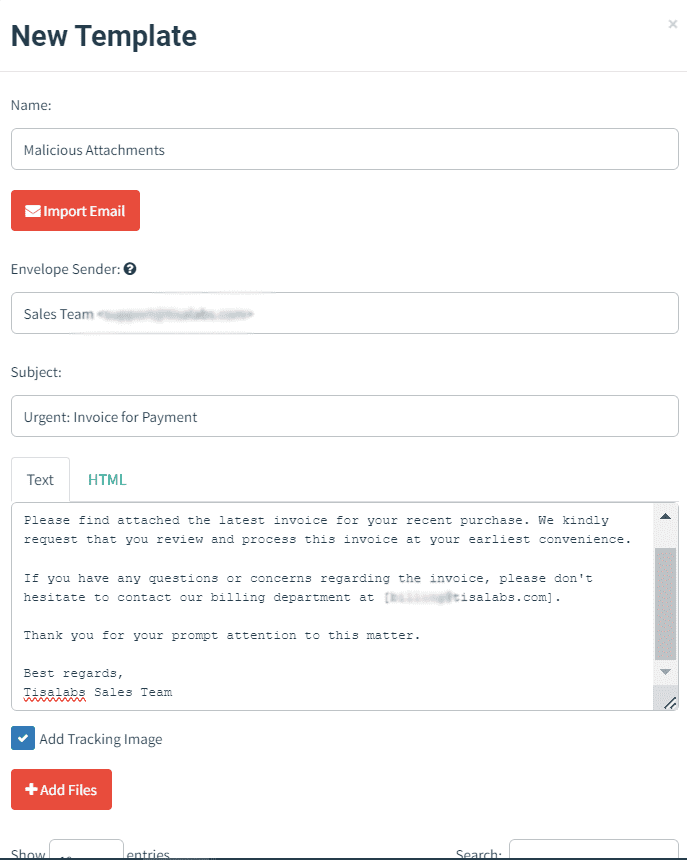
Step 2: Attach Malicious File
Attach a simulated malicious file to the email, ensuring it resembles authentic attachments that users commonly encounter.
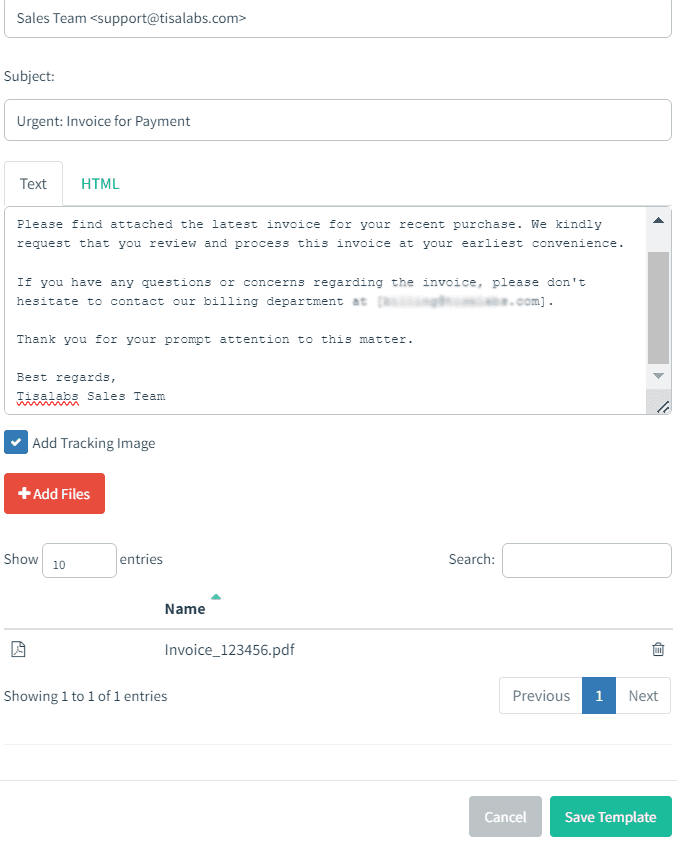
Develop a landing page designed to prompt users to interact with the attached file. This page can simulate a legitimate platform for viewing the attached document.
Step 1: Create Simple Landing Page
Design a basic landing page with a preview of the attached file, encouraging users to click for further details.
Then it’s the part to create the landing page for our phishing campaign. We created just a simple page to review the invoice , and we didn’t aim to capture any data from it , our purpose is to make sure that the target user clicks and opens the attachment in the email we sent.
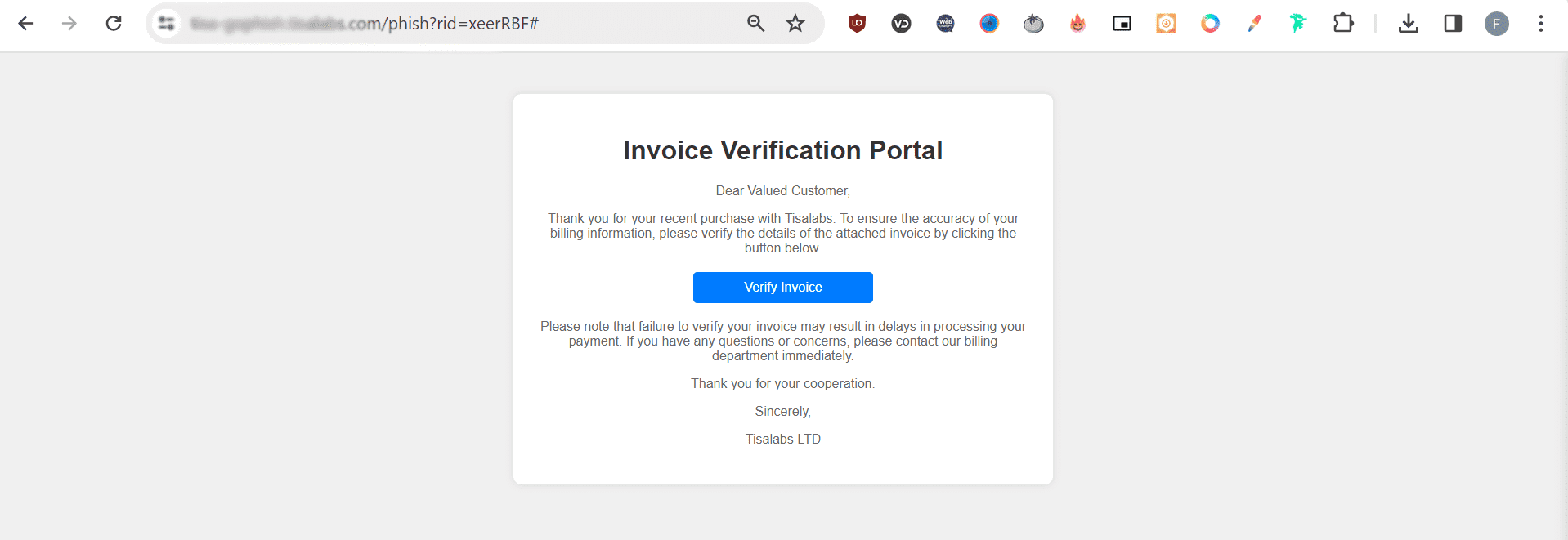
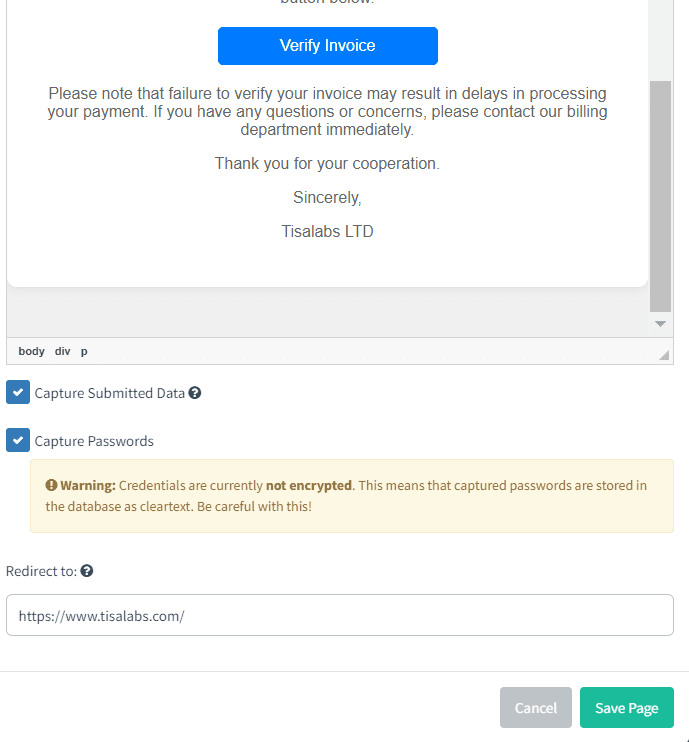
This is our landing page, Everything is ready now. It’s time to start the phishing campaign.
Launch the phishing campaign to send the malicious email to the target user group.
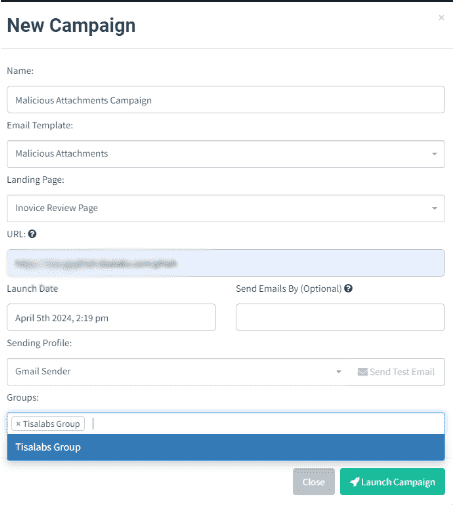
Step 1: Start Campaign
Initiate the campaign, ensuring the target user group receives the phishing email with the malicious attachment.
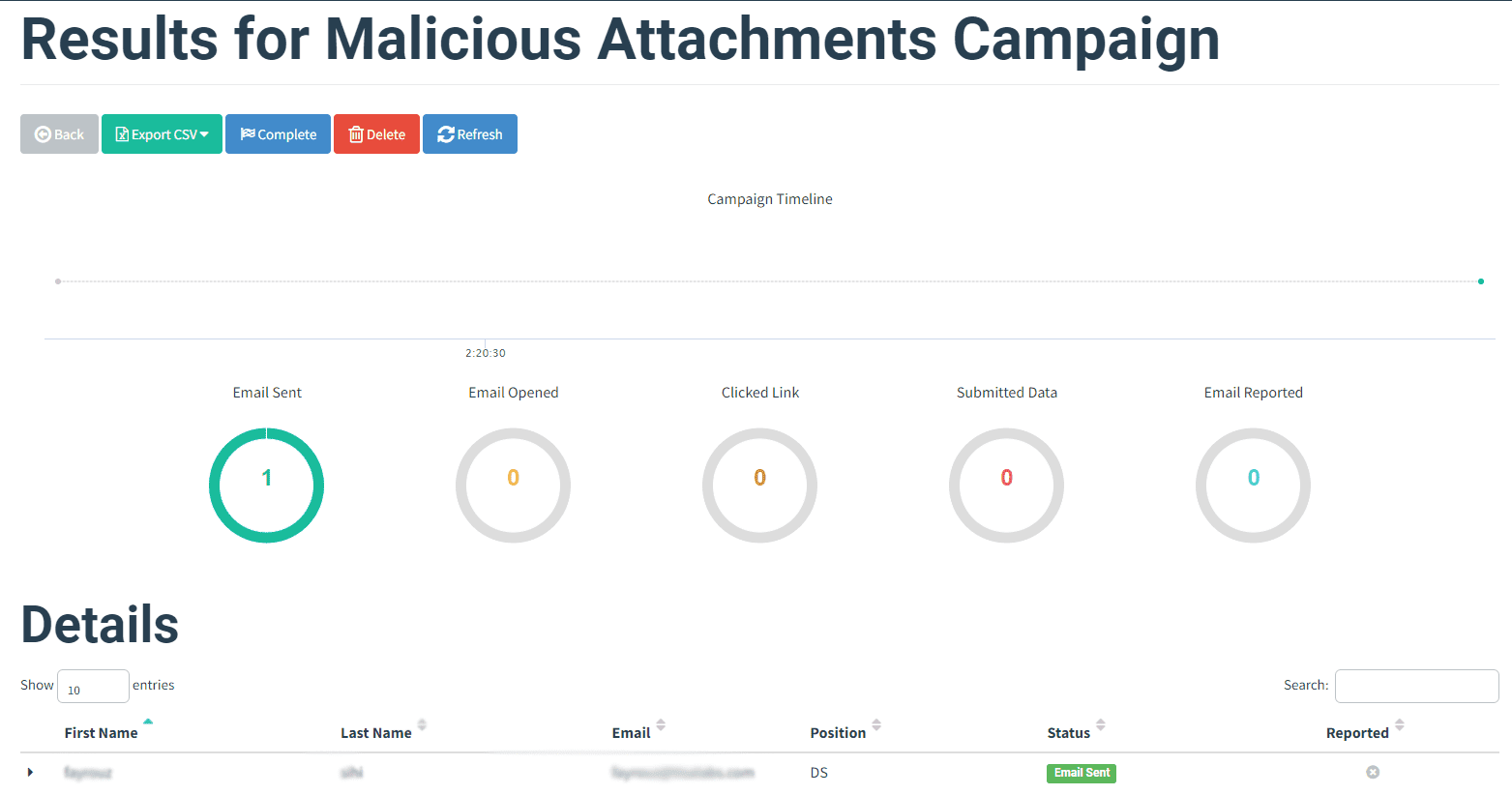
Monitor user interactions with the phishing email and attachment to gauge response rates.
Step 1: Review Email Content
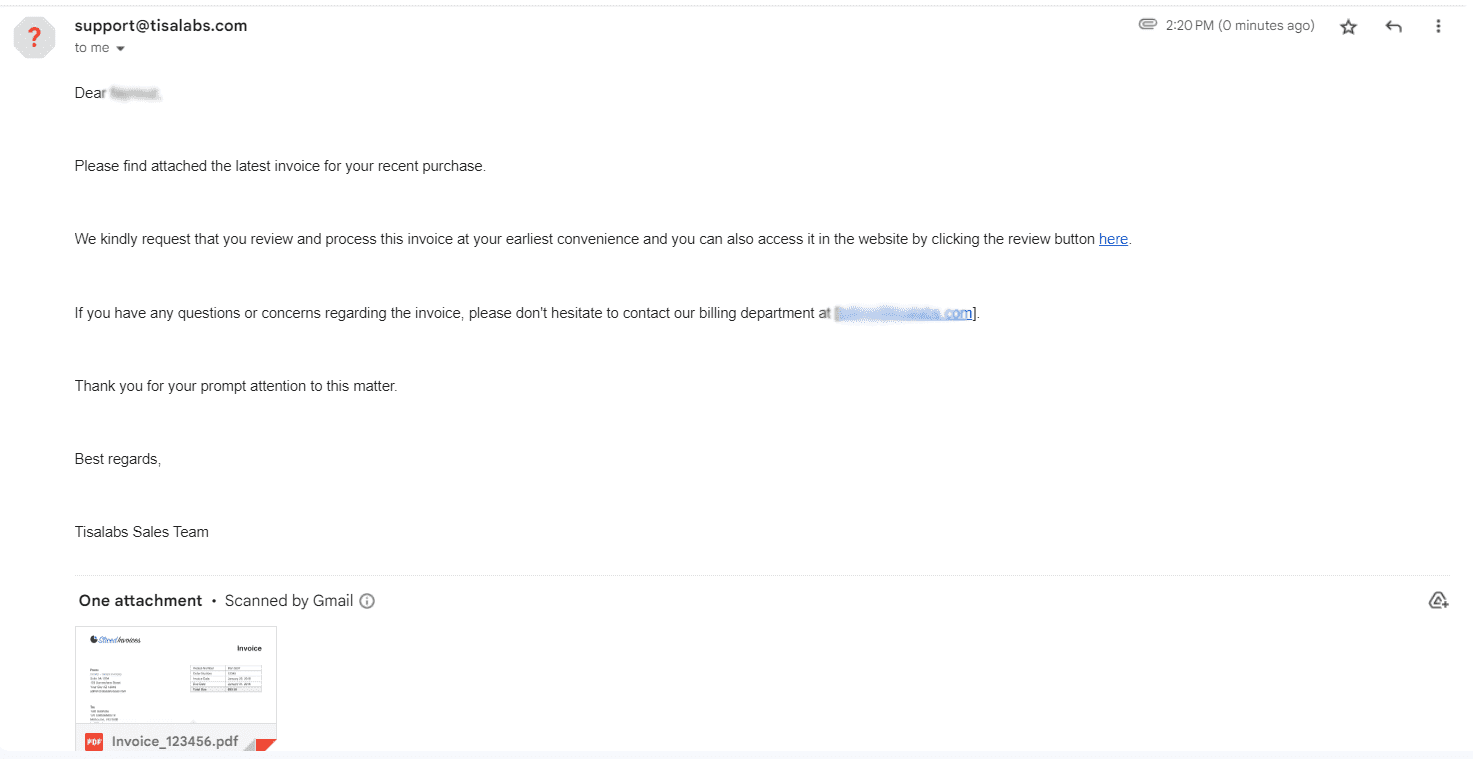
Examine how the phishing email appears in recipients' inboxes and assess its persuasive elements.
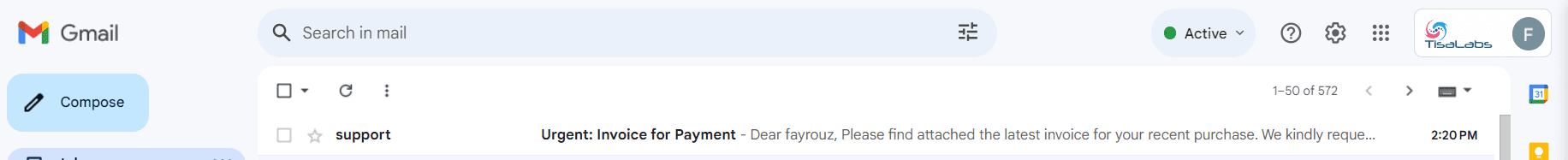
Step 2: Open Email
Open the email to view its content and verify the presence of the attached malicious file.
Assess user engagement with the landing page and the attached file.
Step 1: Click on Landing Page Link
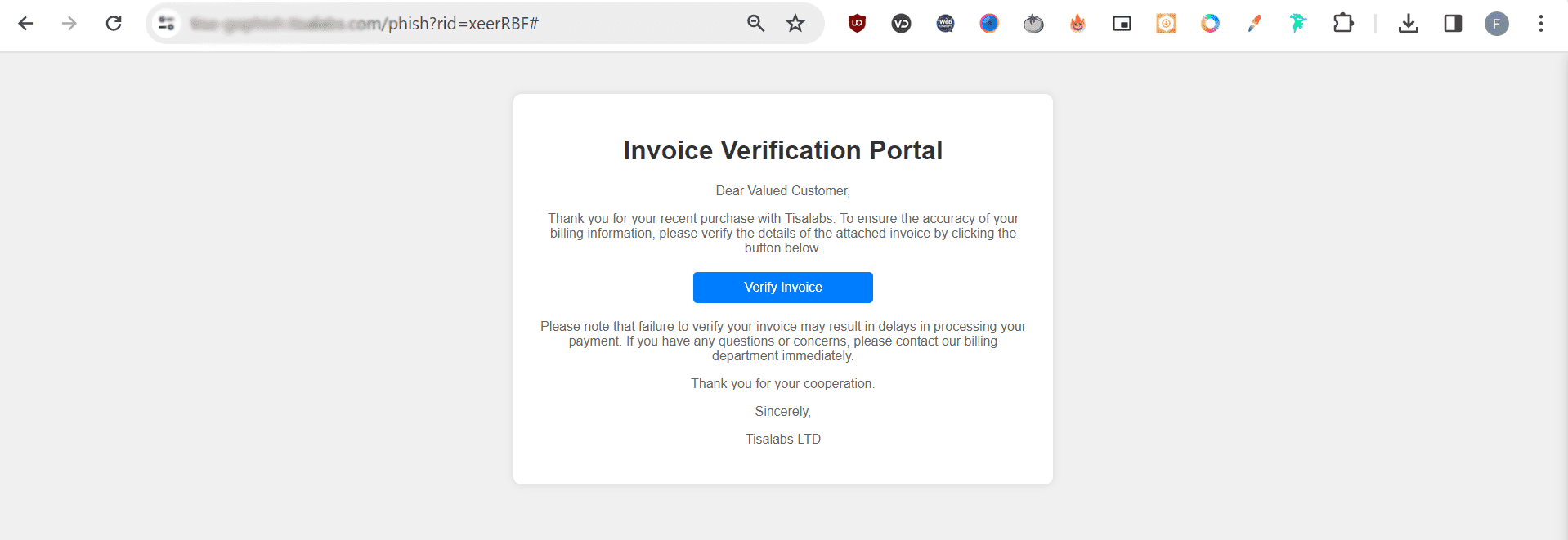
Click on the link provided in the email to access the landing page and interact with the attached file.
Step 2: Evaluate Landing Page
Review the landing page to ensure it effectively encourages users to open the attached file.
Analyze campaign results to determine the effectiveness of the phishing attack.
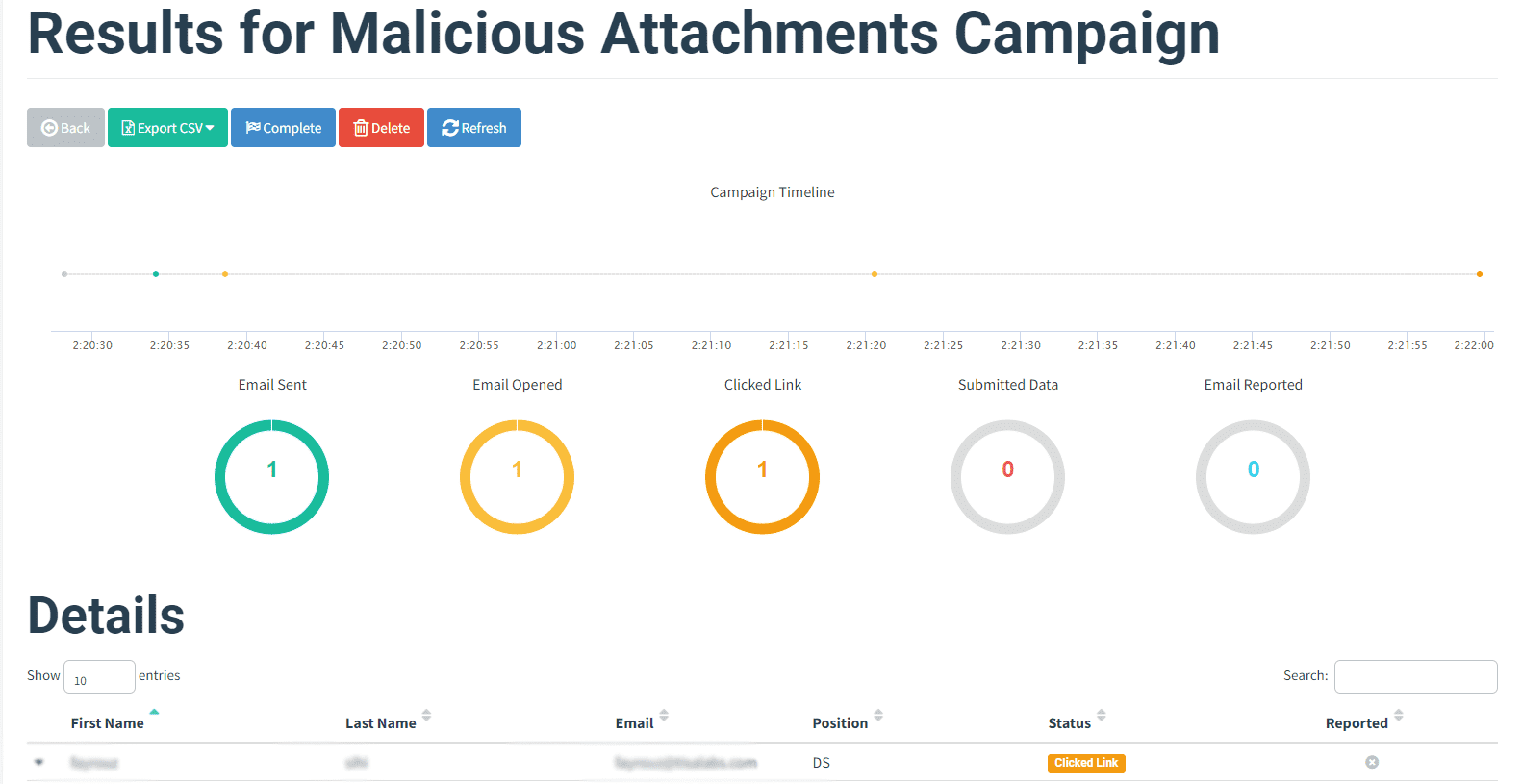
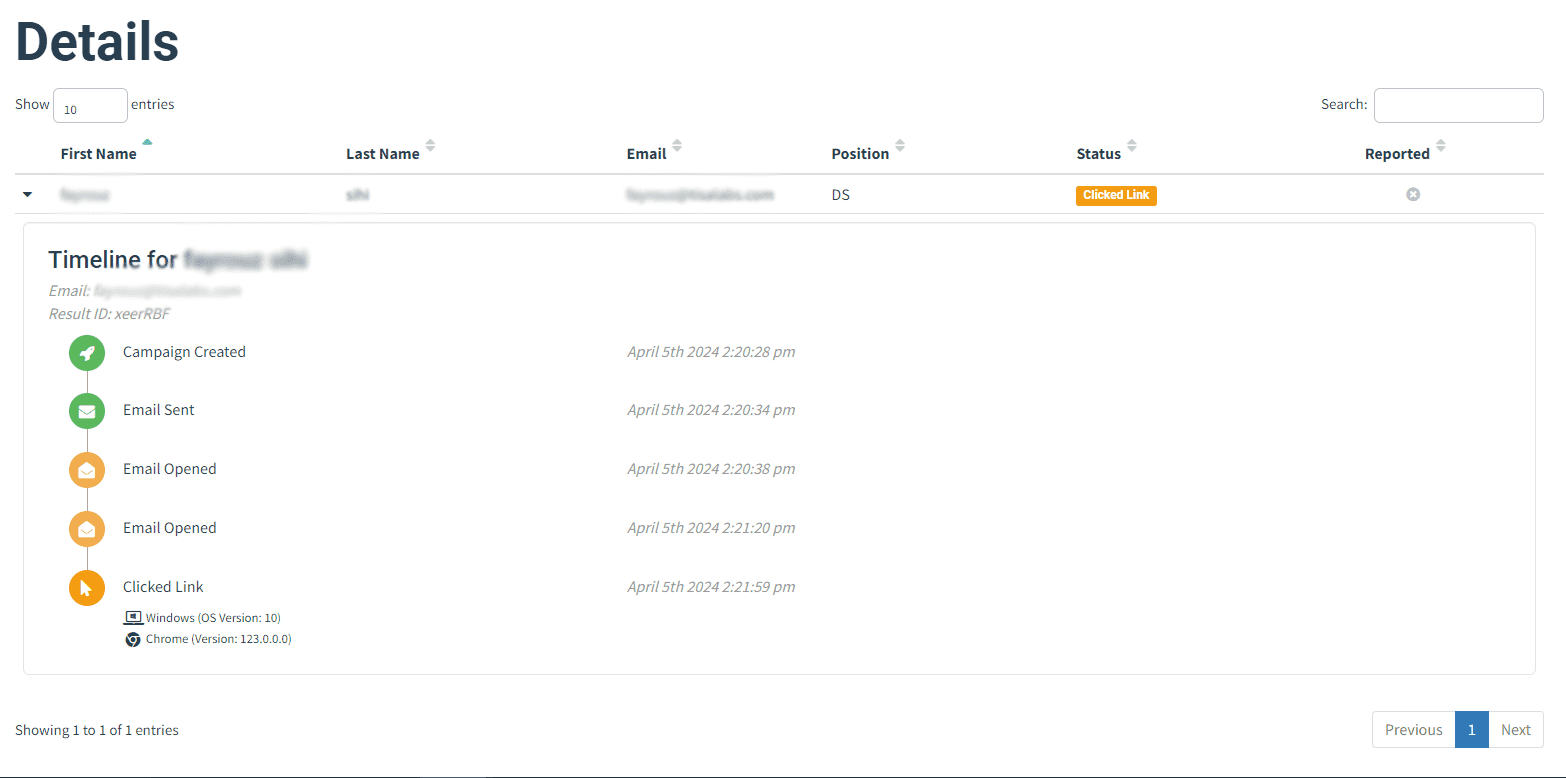
Step 1: Review Campaign Metrics
Monitor campaign metrics, such as email open rates and attachment interaction rates, to assess user susceptibility.
 Q
Q
Step 2: Assess Impact
Evaluate the impact of the phishing campaign and identify areas for improvement in future simulations.
By following this tutorial, you've gained insights into executing a phishing campaign with malicious attachments. Remember to prioritize cybersecurity awareness and implement robust defense mechanisms to mitigate the risks associated with phishing attacks.
If you still can't find an answer to what you're looking for, or you have a specific question, open a new ticket and we'd be happy to help!
Contact Us