Tisalabs Knowledge Base
In this tutorial, we'll explore how to execute a phishing email attack centered around fake promotions or offers. By following these steps, you'll gain insights into crafting convincing phishing emails and creating deceptive landing pages to capture user credentials.
To begin, establish a sender profile that appears legitimate to recipients. This profile will be used to send spear phishing emails to target users.
Step 1: Define Sender Profile
Choose an authentic-looking email address and ensure the username is convincing.

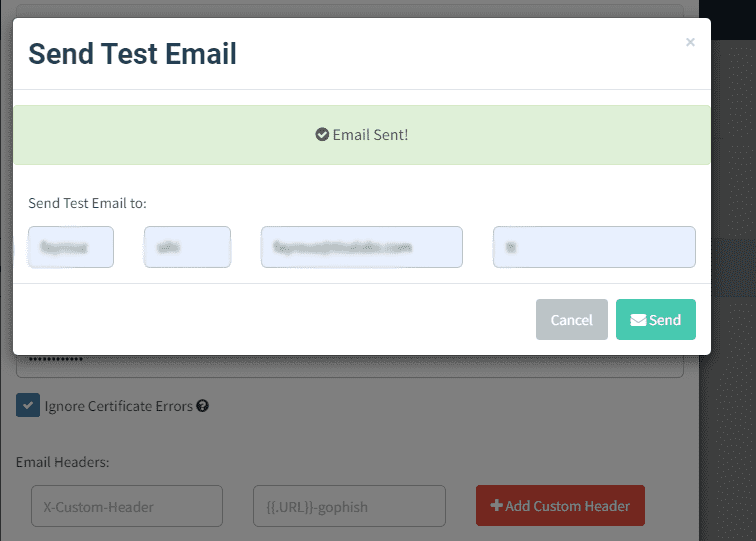
Step 2: Test Configuration
Send a test email to verify the configuration and ensure successful delivery.
Step 3: Save Sender Profile
Once satisfied with the sender profile, save it for future use across all campaigns.
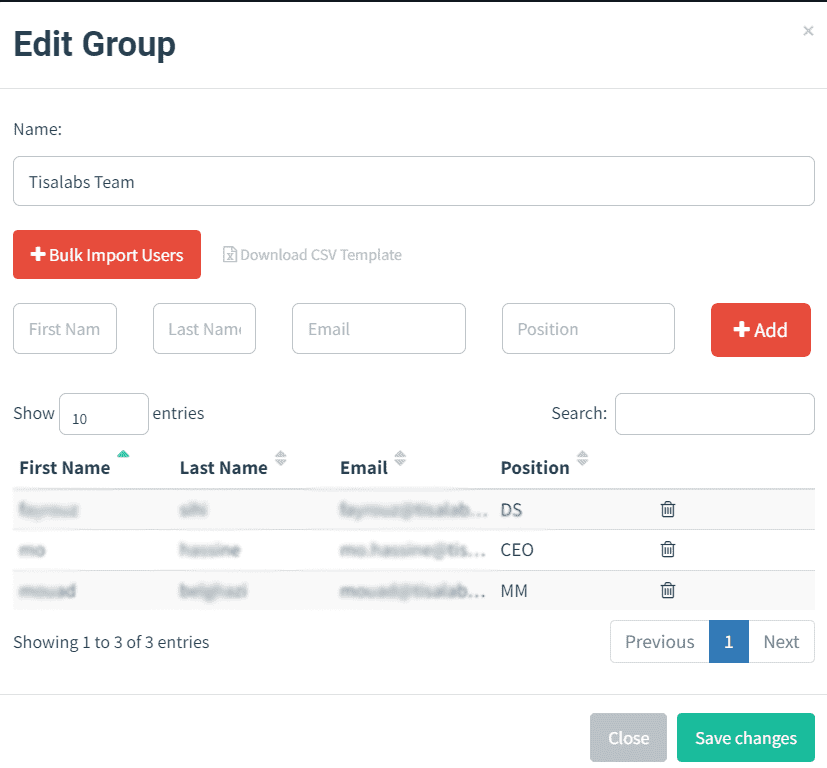
Assign target users for the phishing campaign by creating user groups. This step enables customization and segmentation of the attack.
Step 1: Create Users and Groups
Manually add recipients or import user data from a CSV file.
Design an enticing email template that offers fake promotions or job opportunities to lure recipients into clicking on malicious links.
Step 1: Design Email Content
Compose persuasive email content that prompts users to take action, such as clicking on a link or providing personal information.
Step 2: Example Email
Provide an example of a phishing email offering job opportunities similar to those sent by LinkedIn.
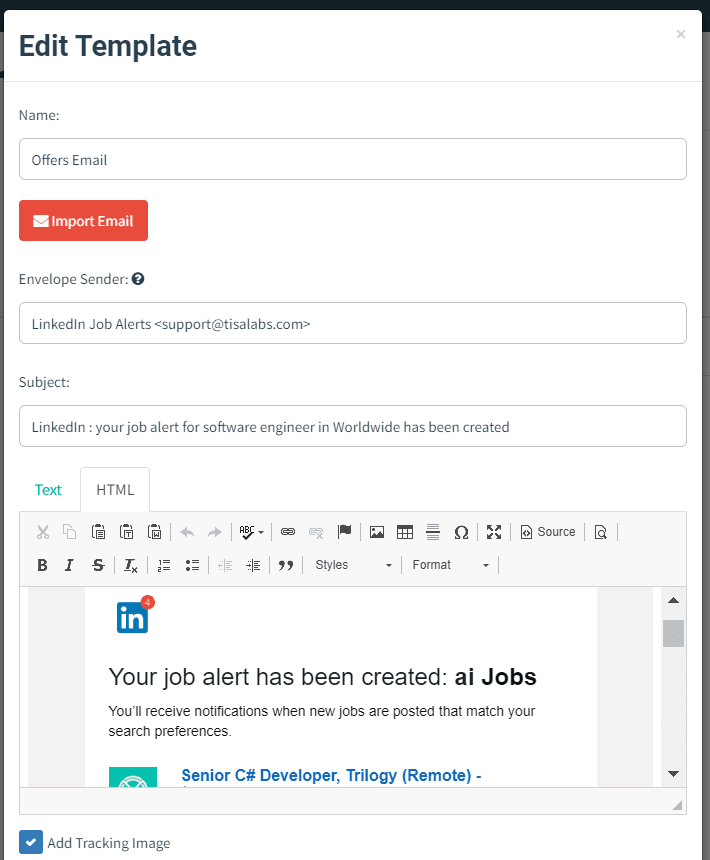
This part is the most important and the content of the email should convince the user to take whatever action you want him to take. We are showing in this email some job offers that LinkedIn sends once you subscribe to a job offer.
Develop a fake landing page that mimics the appearance of a legitimate website, such as LinkedIn, to capture user credentials.
Step 1: Develop Landing Page
Design a phishing website that closely resembles the targeted platform, ensuring authenticity to enhance user deception.
Step 2: LinkedIn Platform Example
Create a fake login page for LinkedIn to capture user credentials.
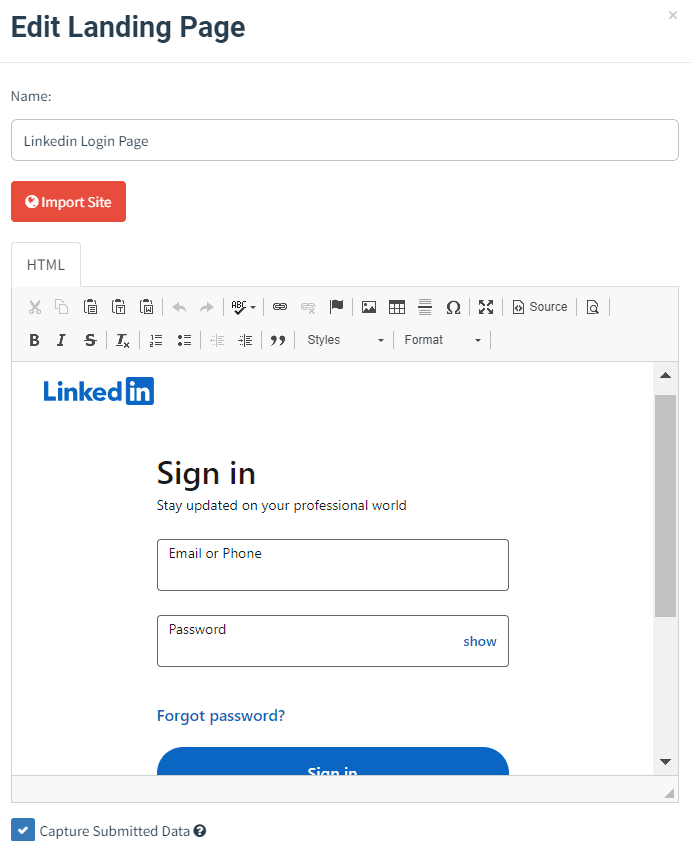
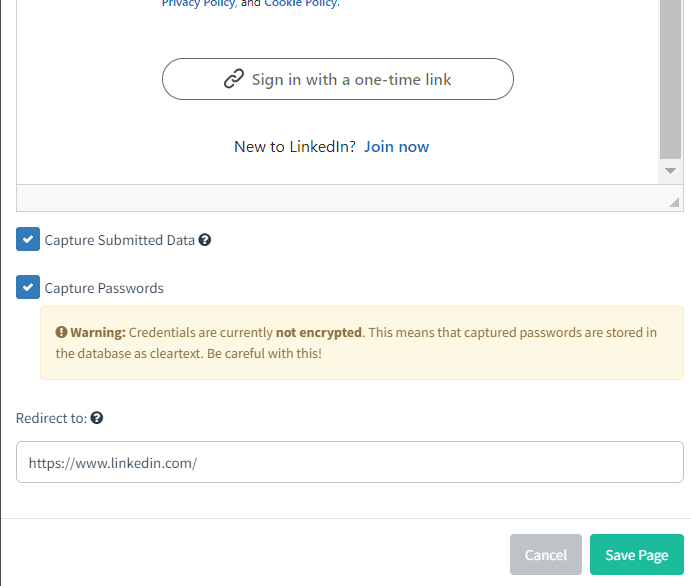
Once created it will show as follows:
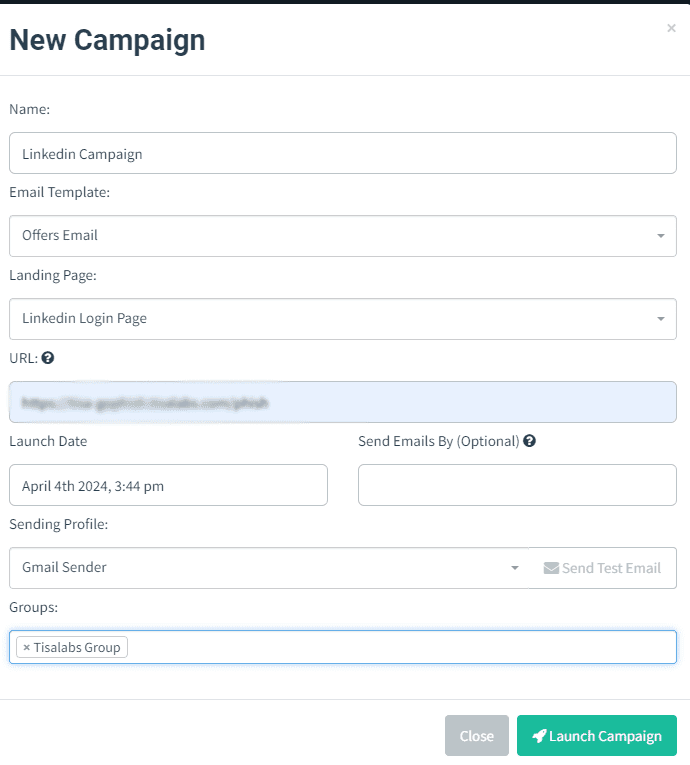
Launch the phishing campaign and monitor its progress from the dashboard.
Step 1: Start Campaign
Navigate to the campaigns section and initiate a new campaign, configuring settings as required.
Step 2: Monitor Dashboard
Track campaign results from the dashboard, monitoring user interactions and email open rates.
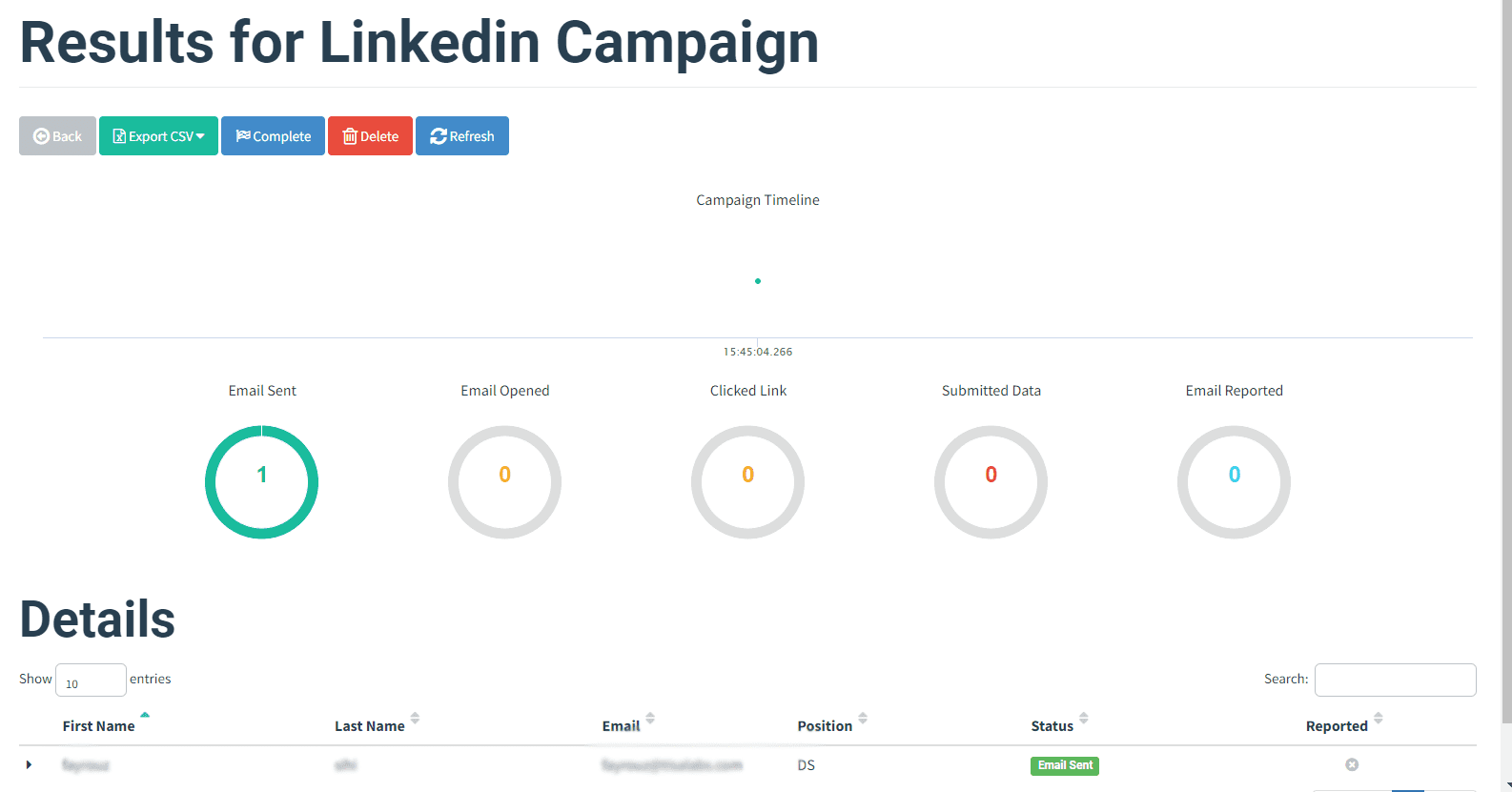
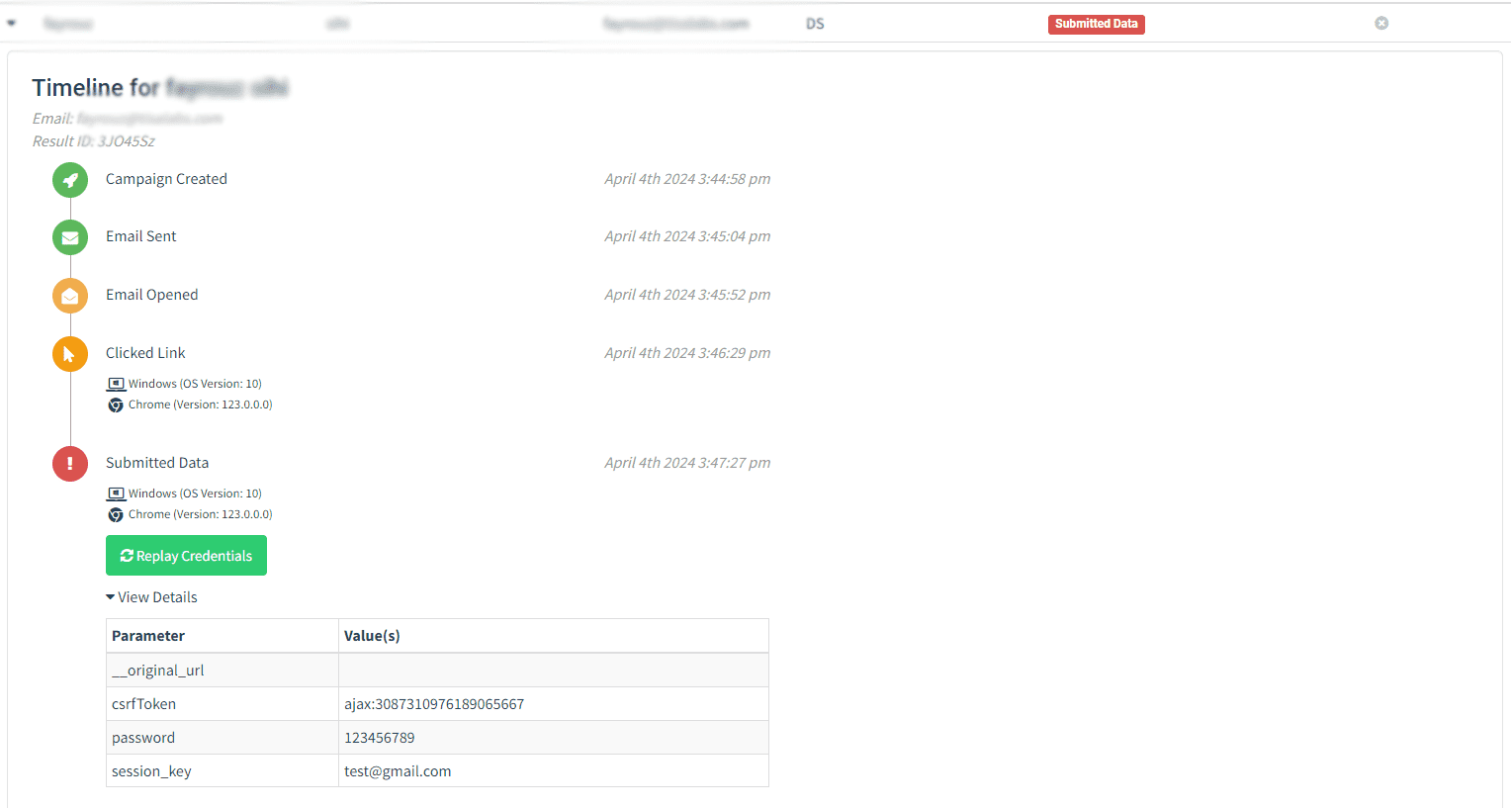
Review the outcomes of the phishing campaign, analyzing data collected from user interactions and assessing its effectiveness.
Step 1: Email Appearance
Inspect how the phishing email appears in recipients' inboxes.
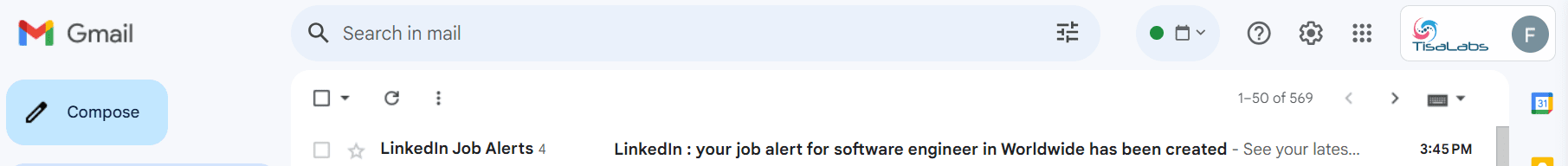
Step 2: Email Content
Review the content of the phishing email to understand its structure and persuasive elements.

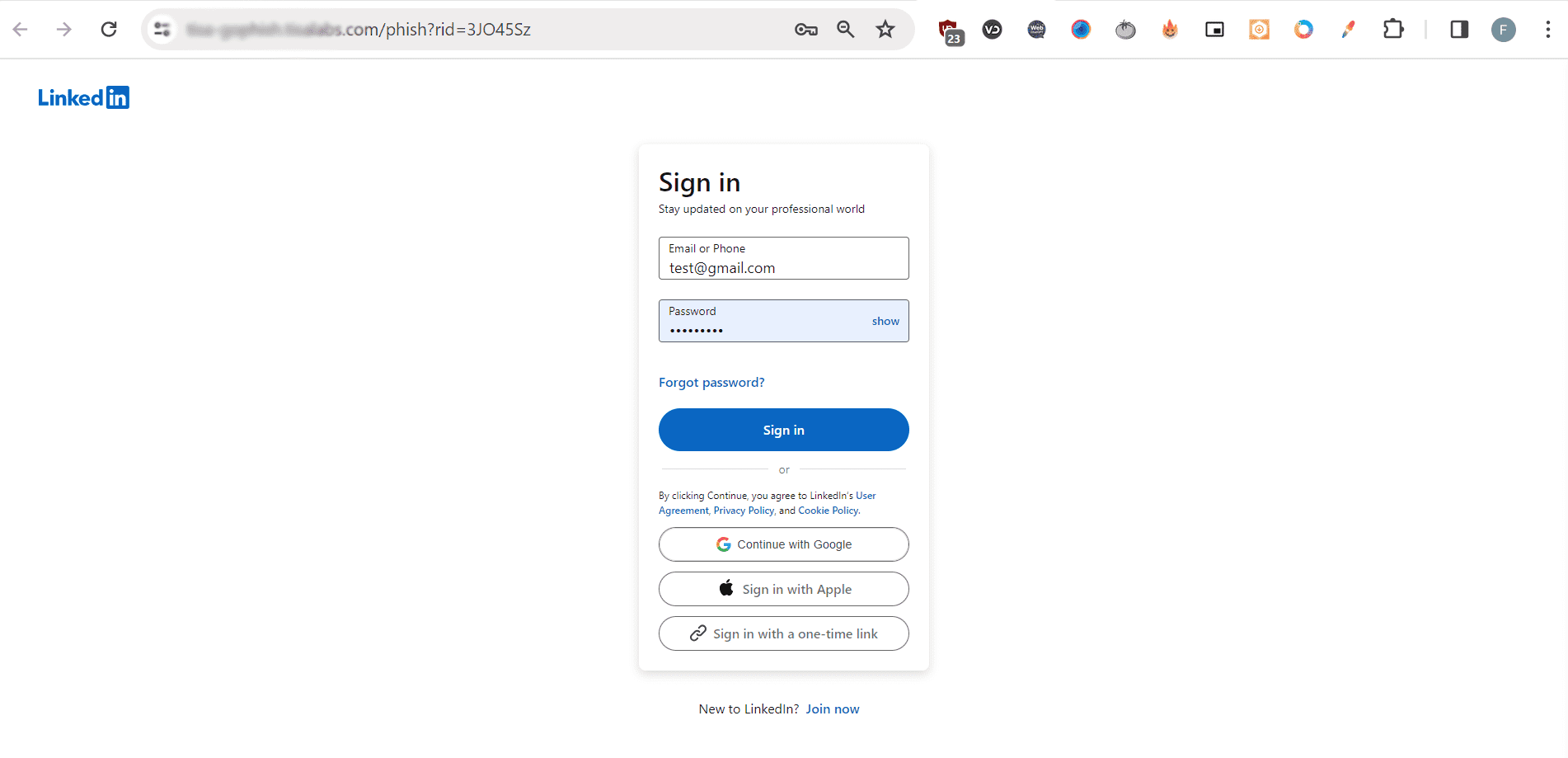
Step 3: Phishing Site
Examine the phishing website and the data collected from users redirected to the site.
Step 4: Data Collection
Analyze the data collected from user interactions, including credentials entered on the phishing site.
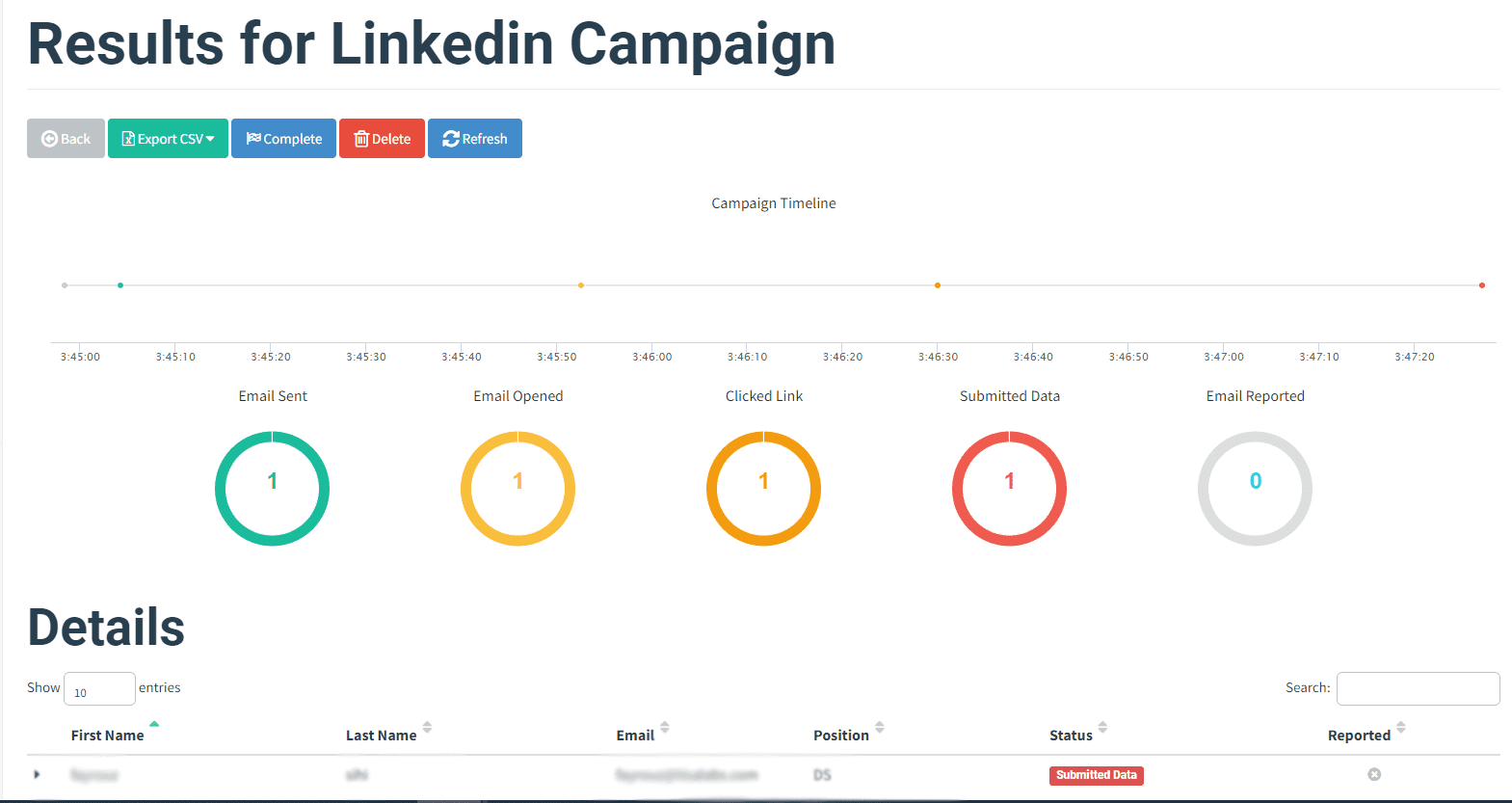
Step 5: Dashboard Insights
Evaluate campaign data available in the dashboard to gauge the success of the phishing attack.
This tutorial helps users to learn how to execute a phishing email attack based on fake promotions or offers. Remember, phishing attacks pose a significant threat to organizations, and it's essential to implement robust security measures and educate users to mitigate risks effectively.
If you still can't find an answer to what you're looking for, or you have a specific question, open a new ticket and we'd be happy to help!
Contact Us